 Northwind Data Recovery, a member of the NoMoreRansom Project / EUROPOL, has been actively fighting ransomware since 2016.
Northwind Data Recovery, a member of the NoMoreRansom Project / EUROPOL, has been actively fighting ransomware since 2016.
In our Ransomware Blog, you can find information about identified strains and the solutions we have found for each of them.
In recent years, there has been a surge in so-called ransomware viruses (Cryptolocker Viruses), which also go by various names such as Cryptowall, STOP/DJVU, Cerber, Phobos, Locky, WannaCry, etc.
In reality, they are incorrectly referred to as “viruses” since they are actually malware (malicious software).
General information about ransomware:
Their operation is more or less the same:
The computer gets infected with ransomware (usually from a deceptive email asking to click on a link or from visiting shady websites). It encrypts the data with AES256 encryption and sends the key to the attacker.
The result is that the files become unusable, with strange extensions (e.g., Scan001.locky or generally scan001.jpg.*) and they are impossible to use.
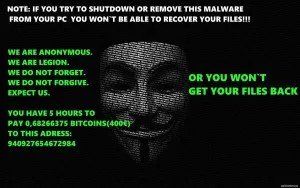
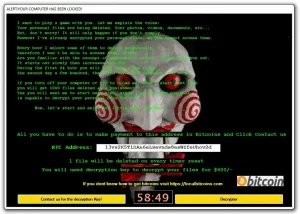
Then the malware creates a splash screen informing the user that the disk’s data has been encrypted and demands a ransom to provide the decryption key. The ransom is usually paid via bitcoin and the entire process is conducted through Tor to prevent the perpetrators from being traced.
It is worth noting that even if the requested amount is paid, there is no guarantee that the perpetrators will provide the key for decryption. Additionally, there is no guarantee that the decryptor they send for decryption will function correctly.
Nor can the “intermediaries” help, avoid them.
It is interesting to note that the first ransomware variants targeted Windows Servers (mainly versions 2003 and earlier) that had the built-in Windows Remote Desktop enabled on the default port (3389). The perpetrators exploited a security flaw in this application, installed the ransomware on the disk, encrypted the data by creating a random 128-bit key which they sent to themselves, and then deleted it from the local disk using sdelete so that it could not be recovered.
Subsequently, the method evolved with more intelligent infection techniques, 256-bit encryption, and non-local key storage, making data decryption impossible without the key.
It should also be emphasized that ransomware usually targets all local disks of the computer, as well as all connected external disks and network disks. Generally, it targets all disks that have a drive letter (C:, D:, X:, etc.), while some more advanced variants even detect and connect to unmapped disks that have not been assigned a drive letter.
How does Ransomware attacks work?
1. The computer is infected by opening links or email attachments or through websites. The malware is installed on the attacked computer. No user consent is requested.
2. The malicious software communicates with the attacker’s server and requests a public RSA key. The public RSA key can encrypt but not decrypt.
3. It then creates an AES key (sometimes creating a key for each file) and encrypts the file using AES encryption. The original file is then deleted.
4. The AES key is encrypted with the Public RSA key and stored somewhere in the encrypted copy of the original file.
5. The victim is informed of the incident and ransom is demanded for decryption.
The Problem:
Without the Private RSA key from the attacker’s server, it is impossible to decrypt the AES keys and, consequently, impossible to decrypt the data.
The Solution – Ransomware Decryption:
The only way to decrypt data affected by Ransomware for which there is no solution is by obtaining the Private RSA keys, and there are two possible scenarios for this to happen:
1. Pay the ransom. The result is not guaranteed, of course, and paying the amount helps spread the problem by creating more similar malicious strains. WE STRONGLY ADVISE AGAINST THIS SOLUTION.
2. Wait. Somehow, the keys may be obtained, and decryption may be possible. There is also no guarantee that this will happen.
There are often flaws or weaknesses in the way the code for these Ransomware functions is written, but finding the flaw and exploiting it requires analysis and Reverse Engineering.
Nowadays, thousands of strains are circulating, more advanced than in the past and often impenetrable. Even someone with no programming knowledge can buy ready-made kits, modify them, and start spreading them to catch unsuspecting or careless users and blackmail them.
Free Evaluation and Ransomware Identification By Northwind Data Recovery:
At Northwind Data Recovery, there are software engineers who have contributed to finding vulnerabilities in many of the circulating strains, making it possible to decrypt the data.
To find out if we can help you decrypt your data, follow these instructions:
- Send us an email with 2-3 encrypted files from your computer.
- Send us in the same email the ransom note left by the Ransomware. This is usually a .txt or .html file named something like help_decrypt.txt, decrypt_info.txt, etc., and is found in all encrypted folders.
- If available, send us an encrypted file along with its normal version that you may have from an older backup.
- Do not send us modified/altered files from other attempts you (or others) may have done.
A specialized technician will then respond with the results of the analysis of the files you sent.
What you should do to avoid Ransomware infection
Since many years, we have compiled a Survival Guide against Ransomware.
It provides some very good tips that you can follow.
You can find it here.

